Sophos UTMでWebセキュリティー対策 第4回 ~Webサーバプロテクション(WAF)~

目次
前回 (第3回) の内容
株式会社ハイパーボックス -HYPER BOX- の相原と申します。
前回は、
- IPS機能の有効化
- 攻撃パターンの選択
- フラット防御の有効化
- ポートスキャン防御の有効化
- 高度な脅威防御(Advanced Threat Protection)の設定
を紹介しました。
第4回となる今回は、Sophos UTMにおけるWebサーバプロテクション(WAF)の設定を紹介していきたいと思います。
| 第1回 | インスタンスの作成から初期設定まで |
| 第2回 | 簡易的なネットワーク構成の構築、ファイアウォールの設定、DNATの設定 |
| 第3回 | ネットワークプロテクション 侵入防御(IPS)の設定、高度な脅威防御(ATP)の設定 |
| 第4回 | Webサーバプロテクション(WAF)の設定 |
| 第5回 | Webサーバプロテクション(WAF)とロードバランシングの設定 |
第4回 Webサーバプロテクション(WAF)の設定
今回の概要
ファイアウォールプロファイルの作成
デフォルトのプロファイルをコピーし、モードを変更
バックエンドWebサーバの作成
WAFで保護する対象のWebサーバを設定
新規仮想Webサーバの作成
仮想Webサーバ (リバースプロキシ) を作成
WAFの動作確認用にWordPressをインストール
バックエンドWebサーバにWordPressをインストール
WAFのライブログ確認とフィルタルールのスキップ設定
WAFのライブログを確認、誤検出となるルールをスキップするようにフィルタを設定
インフラストラクチャルールについて
「フィルタールールをスキップ」リストにルールIDを追加する際の注意事項
WAFの動作確認
「wordpress-server」へ攻撃、拒否されるか確認
ファイアウォールプロファイルの作成
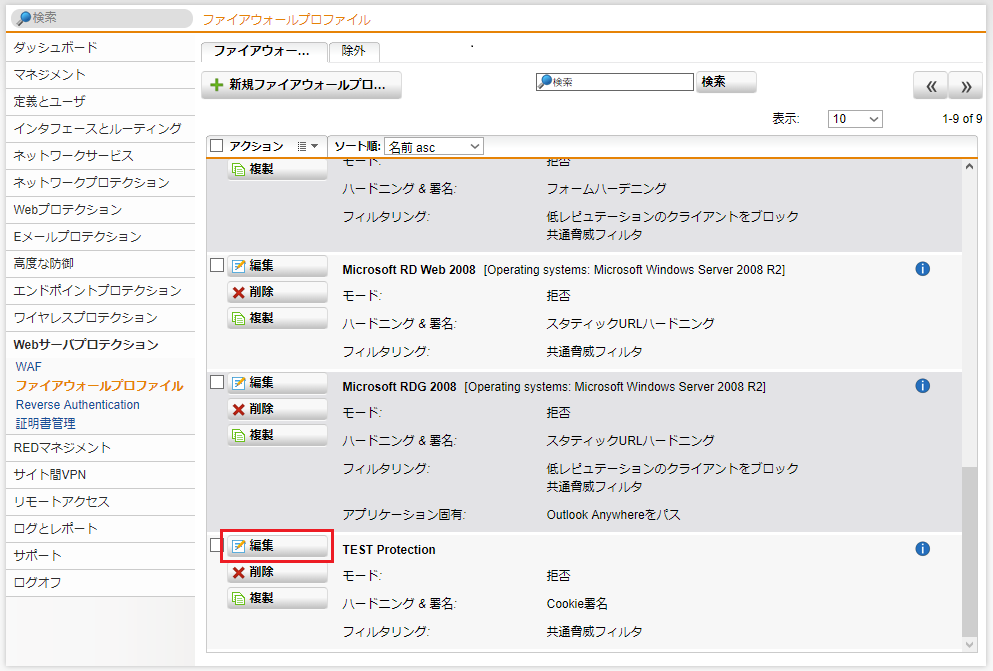
デフォルトのファイアウォールプロファイルをコピーする
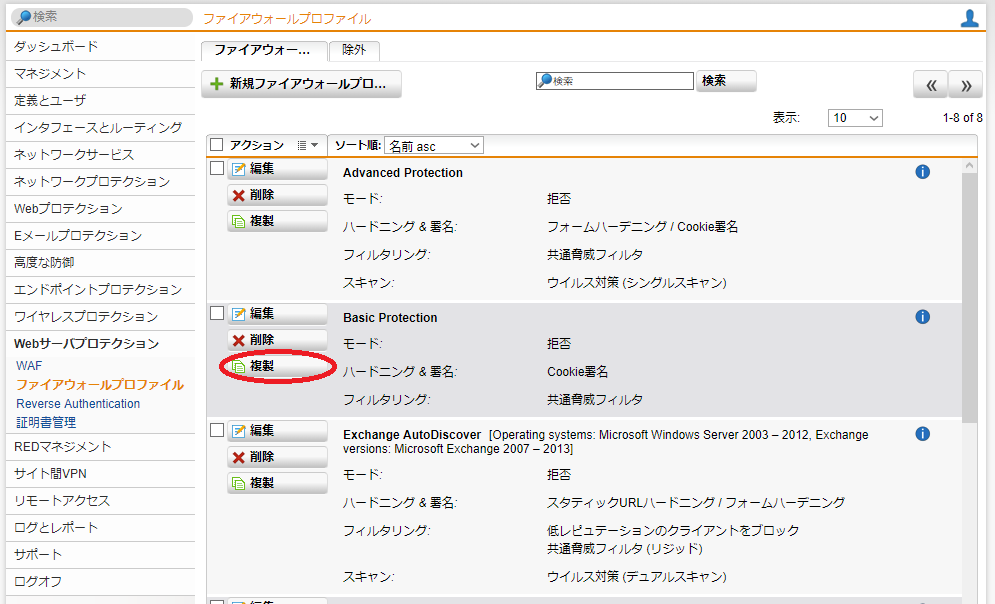
- Webサーバプロテクション > ファイアウォールプロファイル > ファイアウォールプロファイル タブをクリックし、「Basic Protection」の「複製」ボタンをクリックします。

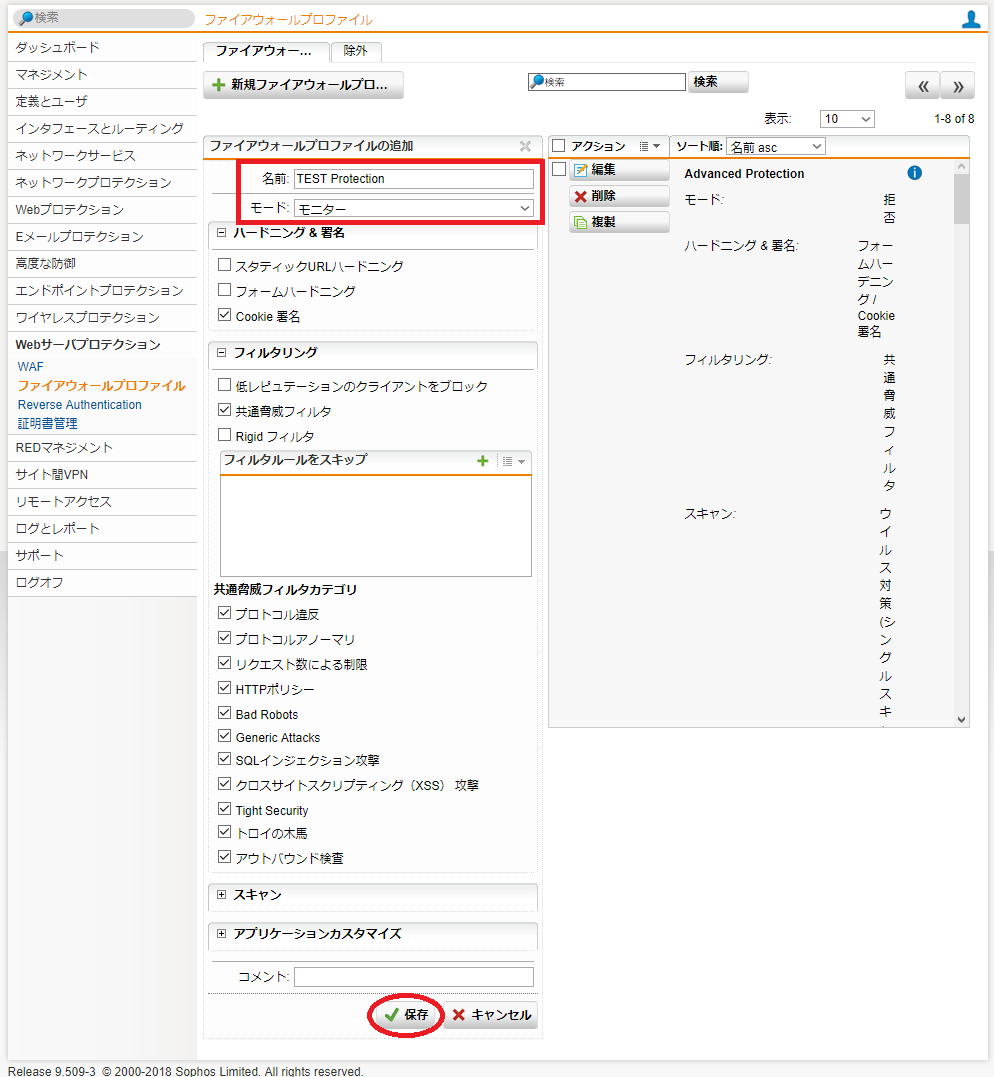
- 名前は任意ですが、今回は「TEST Protection」とします。モードは「モニター」にし、その他の項目はデフォルトのままで「保存」ボタンをクリックします。

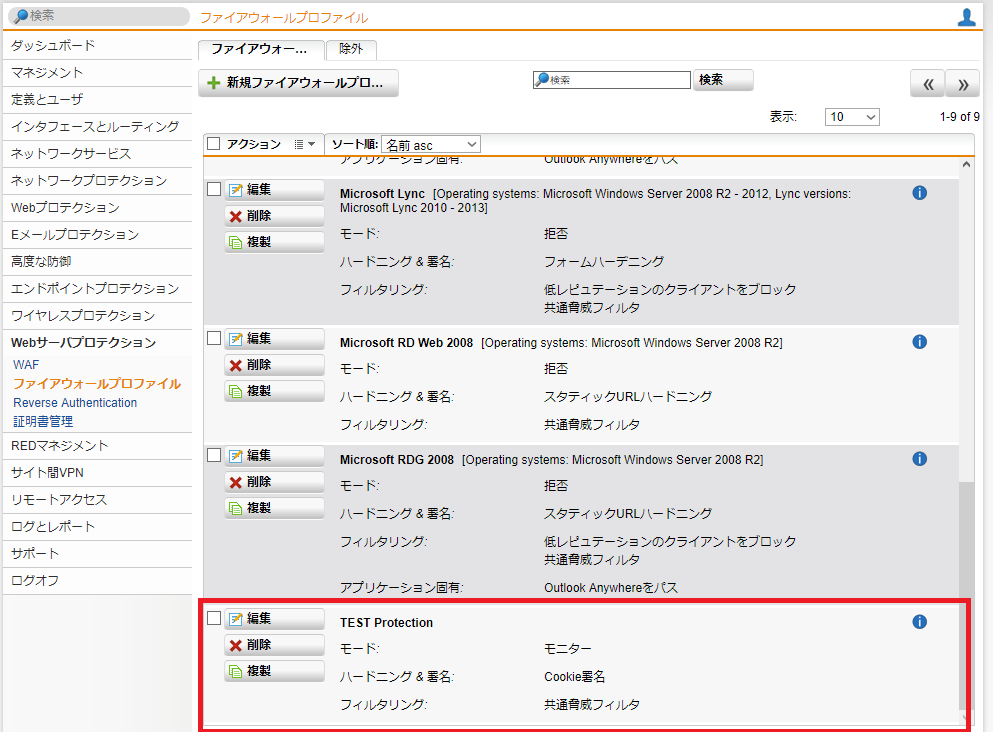
- コピーしたファイアウォールプロファイルが作成されたか確認します。

バックエンドWebサーバの作成
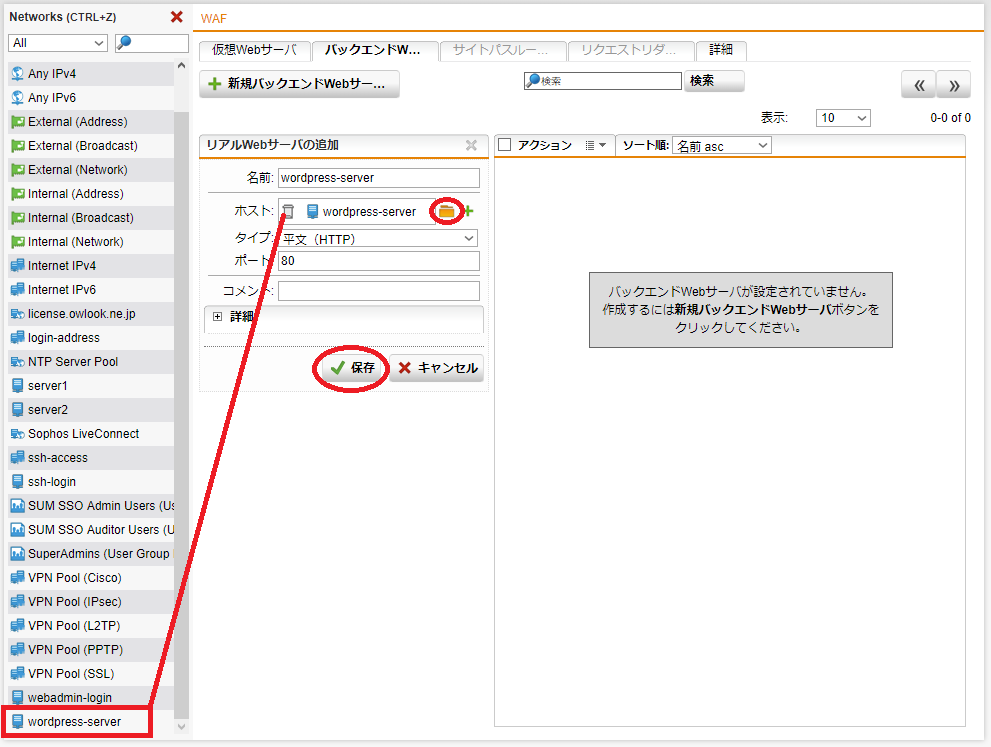
第2回の記事で作成した「wordpress-server」をバックエンドWebサーバに設定
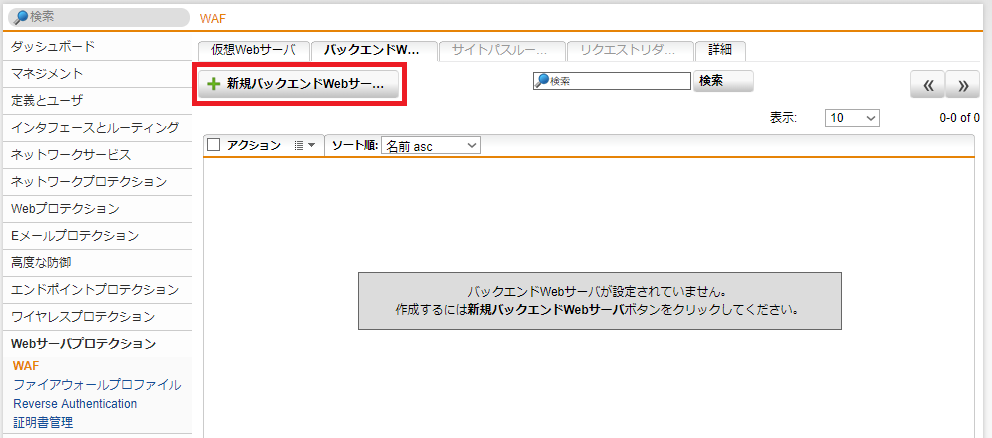
- Webサーバプロテクション > WAF > バックエンドWebサーバ タブをクリックし、「+ 新規バックエンドWebサーバ」をクリックします。

- 名前は任意ですが、今回は「wordpress-server」とします、ホストはフォルダアイコンをクリックして、オブジェクトから第2回の記事で作成した「wordpress-server」をドラッグ&ドロップし、タイプは「平文 (HTTP)」を選択、ポートは「80」のままで「保存」ボタンをクリックします。

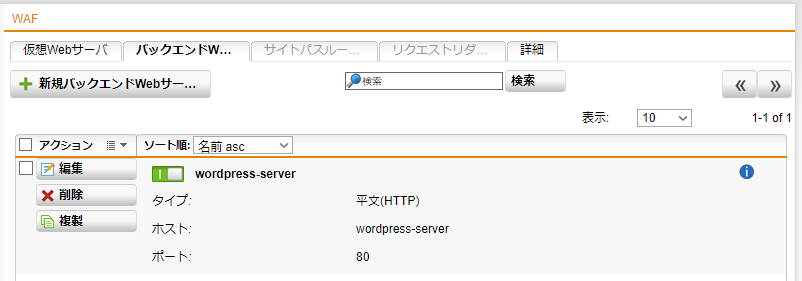
- バックエンドWebサーバが作成されたか確認します。

仮想Webサーバの作成
「wordpress-server」用の仮想Webサーバを作成
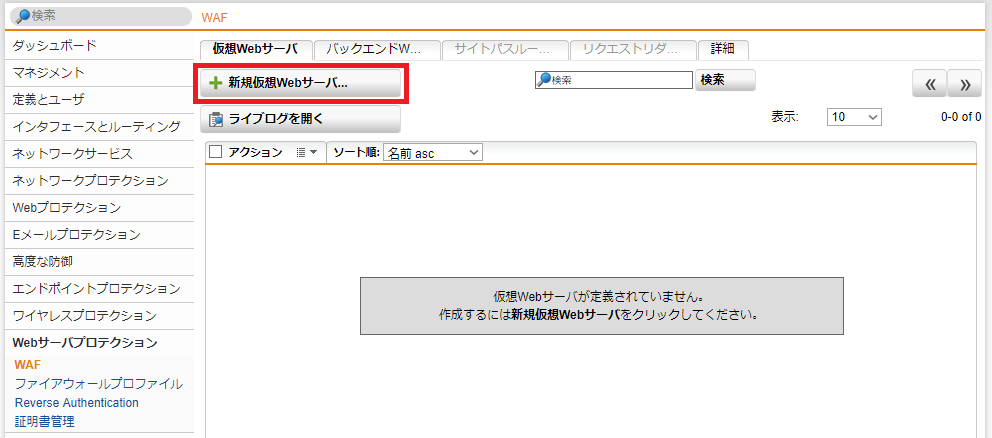
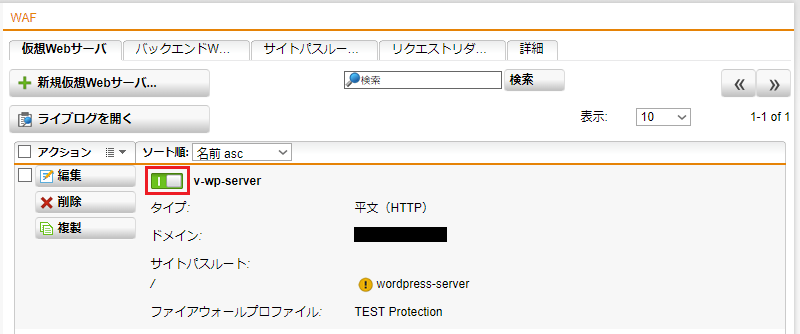
- Webサーバプロテクション > WAF > 仮想Webサーバ タブをクリックし、「+ 新規仮想Webサーバ」をクリックします。

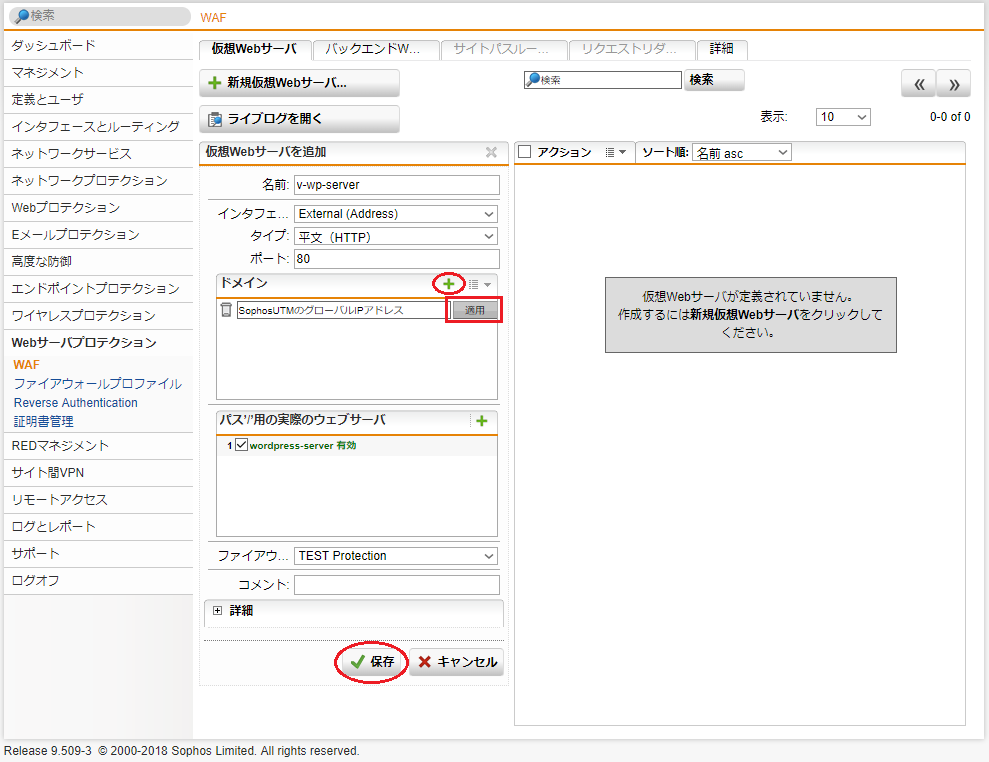
- 名前は任意ですが、今回は「v-wp-server」とします、インタフェースは「External (Address)」を選択し、タイプは「平文 (HTTP)」を選択、ポートは「80」のままで、ドメインの「 + 」をクリックして、Sophos UTM に付与されたグローバルIPアドレスを入力後、隣の「適用」ボタンをクリックします。
「パス'/'用の実際のウェブサーバ」で「wordpress-server」にチェックを入れ、ファイアウォールプロファイルは先ほど作成した「TEST Protection」を選択し、「保存」ボタンをクリックします。

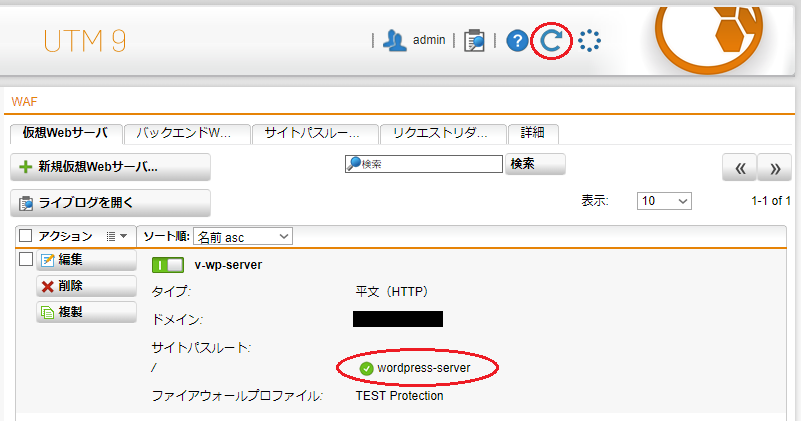
- トグルスイッチをクリックして仮想Webサーバを有効にします。

- リロードをクリックし、仮想Webサーバと紐づけられたバックエンドWebサーバが有効(緑)になっていることを確認します。

仮想Webサーバへのアクセス制御
今回はテスト用ですので、サイトの表示確認を行うPCの送信元IPアドレスのみ、TCP-80 への通信を許可する設定とします。また、Sophos UTM のトラフィック・フローについてですが、仮想Webサーバへの通信は「ネットワークプロテクション」の「ファイアウォール」を通りません。「インターネット」→「共有セグメント」→「IPS」→「仮想Webサーバ」→「バックエンドWebサーバ」というフローになります。
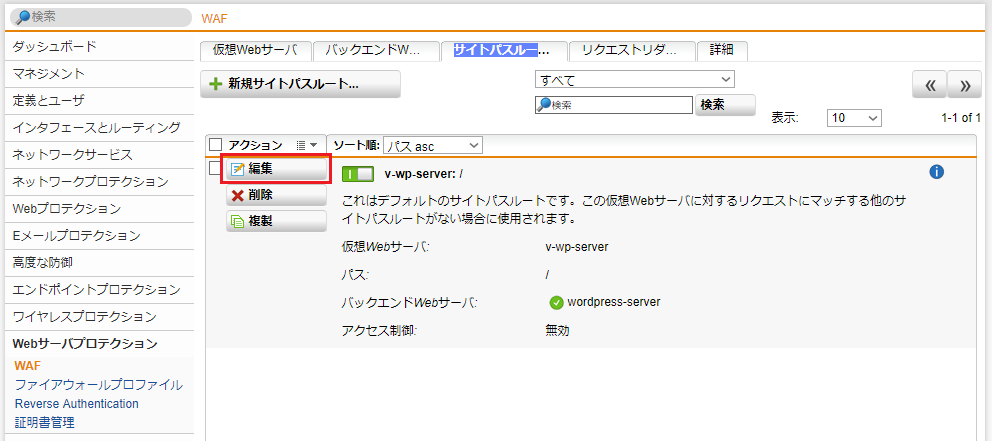
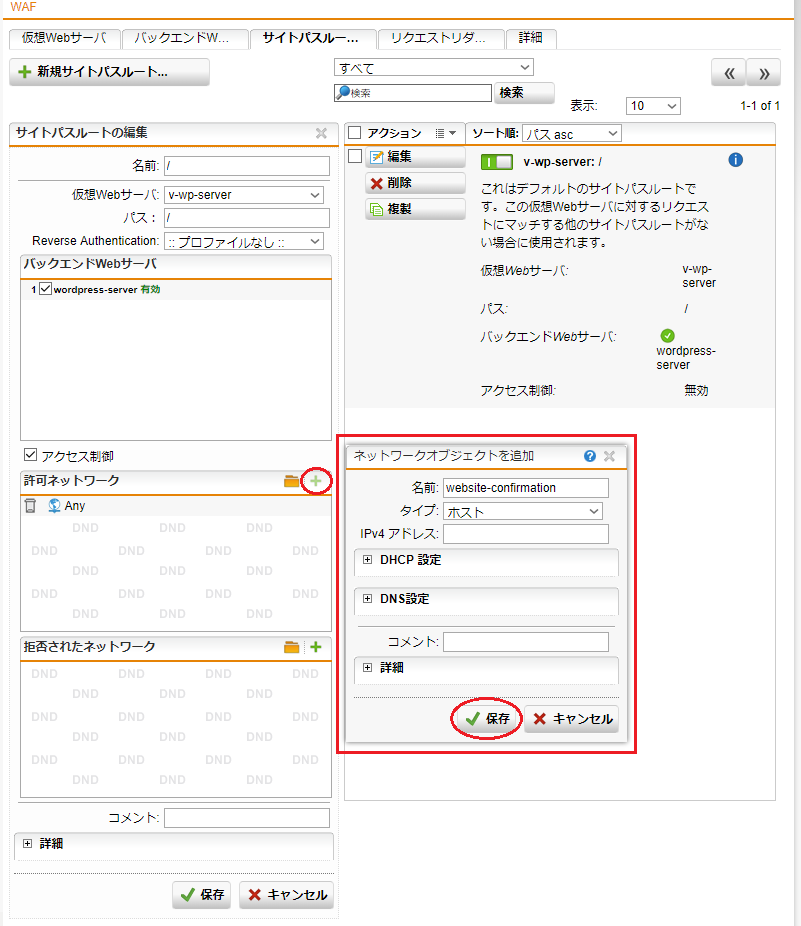
- Webサーバプロテクション > WAF > サイトパスルーティング タブをクリックし、「v-wp-server: /」の「編集」をクリックします。

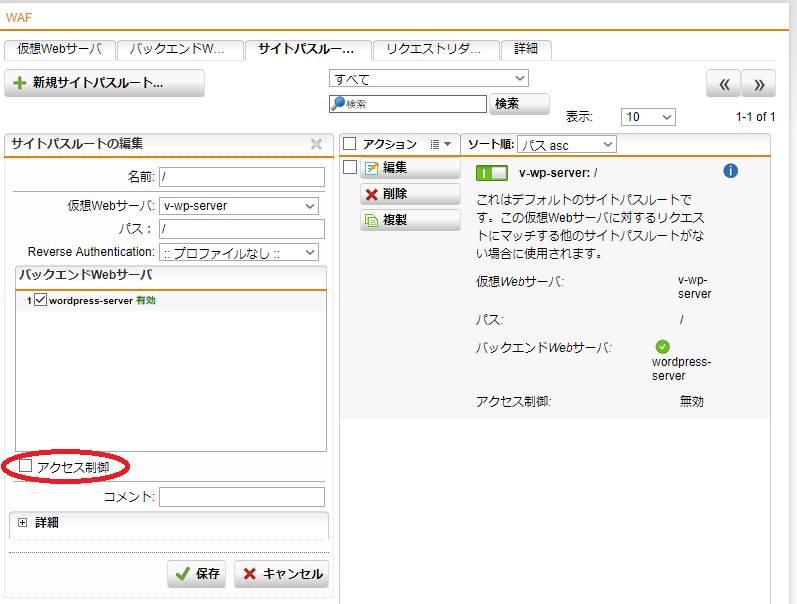
- 「アクセス制御」にチェックを入れます。

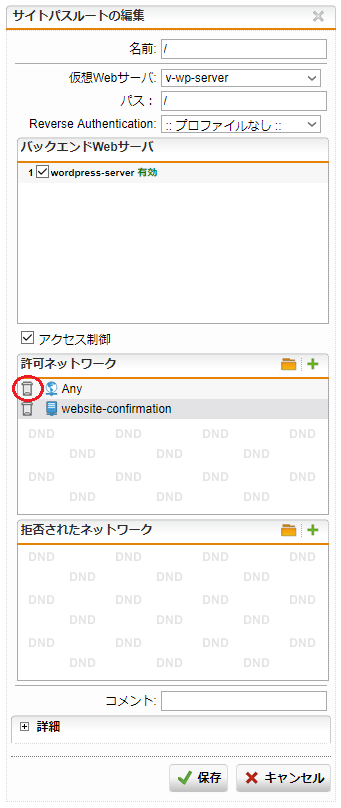
- 「許可ネットワーク」の「 + 」をクリックし、「ネットワークオブジェクトを追加」を開きます。名前は任意ですが、今回は「website-confirmation」とします、タイプは「ホスト」を選択し、IPv4アドレスにサイトの表示確認をするPCの送信元IPアドレスを入力して、「ネットワークオブジェクトを追加」内の「保存」ボタンをクリックします。

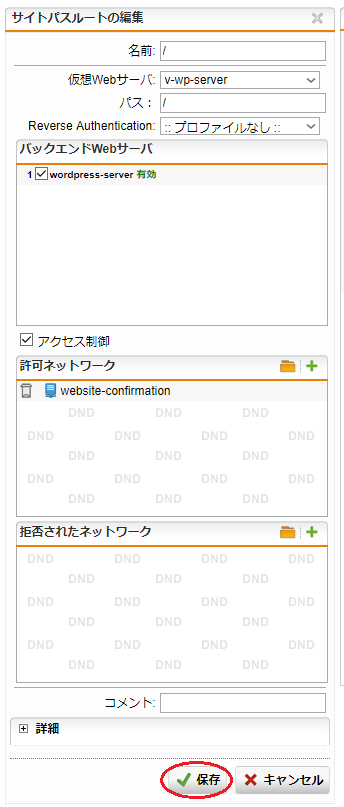
- 「許可ネットワーク」のデフォルトで入っている「Any」をゴミ箱のアイコンをクリックして削除します。

- 「保存」ボタンをクリックします。

WAFの動作確認用にWordPressをインストール
バックエンドWebサーバにWordPressをインストールします。
LAMP環境の構築やWordPressのインストールはネット上に情報が潤沢にあるため、本記事では省略します。
本記事における例として使用するOS・ソフトウェアの各バージョンは下記になります。
[root@wordpress-server ~]# cat /etc/redhat-release CentOS Linux release 7.5.1804 (Core) [root@wordpress-server ~]# apachectl -v Server version: Apache/2.4.6 (CentOS) Server built: Jun 27 2018 13:48:59 [root@wordpress-server ~]# mysql -V mysql Ver 14.14 Distrib 5.7.22, for Linux (x86_64) using EditLine wrapper [root@wordpress-server ~]# php -v PHP 5.4.16 (cli) (built: Apr 12 2018 19:02:01) Copyright (c) 1997-2013 The PHP Group Zend Engine v2.4.0, Copyright (c) 1998-2013 Zend Technologies [root@wordpress-server ~]# cat /var/www/html/wp/wp-includes/version.php | grep wp_version * @global string $wp_version $wp_version = '4.9.8';
WAFのライブログ確認とフィルタルールのスキップ設定
Sophos UTM のWAFはデフォルト設定が厳格なため、誤検出を防ぐために下記の作業が必要になります。
- WAF (ファイアウォール プロファイル) モード:モニターで設定
- Webサイトへ正常系アクセス試験を一通り実施
- 検出されたルールIDを「フィルタルールをスキップ」リストへ追加
サイトへ正常系アクセス、ライブログを確認
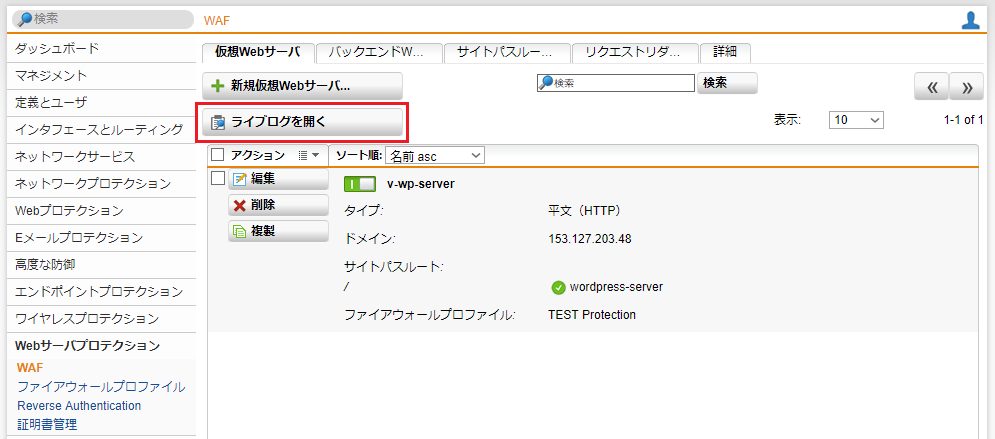
- Webサーバプロテクション > WAF > 仮想Webサーバ タブをクリックし、「ライブログを開く」をクリックするとライブログのウィンドウが新たに開きます。

- 下記のURLへアクセスし、一通りサイト内で行動してみます。
http://Sophos UTM に付与されたグローバルIPアドレス/
http://Sophos UTM に付与されたグローバルIPアドレス/wp-login.php


- サイト内で行動した後のライブログの一部を見てみましょう。
※送信元のIPを「-Source_IP-」、Sophos UTM のグローバルIPを「-Destination_IP-」に変更してあります。
2018:09:20-10:42:24 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "^[\\\\d.:]+$" at REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_protocol_anomalies.conf"] [line "98"] [id "960017"] [rev "2"] [msg "Host header is a numeric IP address"] [data "-Destination_IP-"] [severity "WARNING"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "9"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [tag "http://technet.microsoft.com/en-us/magazine/2005.01.hackerbasher.aspx"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7AJl-yzAAADu6eL8AAABL"]
2018:09:20-10:42:24 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Rule 9d7d648 [id "981172"][file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"][line "157"] - Execution error - PCRE limits exceeded (-8): (null). [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7AJl-yzAAADu6eL8AAABL"]
2018:09:20-10:42:24 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS:load[]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS:load[]: hoverIntent,common,admin-bar,wp-ajax-response,jquery-color,wp-lists,quicktags,jquery-query,admin-comments,svg-painter,heartbeat,"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7AJl-yzAAADu6eL8AAABL"]
2018:09:20-10:42:24 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS:load[]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS:load[]: wp-auth-check,wp-a11y,wplink,jquery-ui-core,jquery-ui-widget,jquery-ui-position,jquery-ui-menu,jquery-ui-autocomplete"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7AJl-yzAAADu6eL8AAABL"]
2018:09:20-10:42:24 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "(.*)" at TX:960017-OWASP_CRS/POLICY/IP_HOST-REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_inbound_blocking.conf"] [line "26"] [id "981176"] [msg "Inbound Anomaly Score Exceeded (Total Score: 9, SQLi=2, XSS=): Last Matched Message: Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Last Matched Data: -Destination_IP-"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7AJl-yzAAADu6eL8AAABL"]
2018:09:20-10:42:24 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "(.*)" at TX:981173-OWASP_CRS/WEB_ATTACK/RESTRICTED_SQLI_CHARS-ARGS:load[]. [file "/usr/apache/conf/waf/modsecurity_crs_inbound_blocking.conf"] [line "26"] [id "981176"] [msg "Inbound Anomaly Score Exceeded (Total Score: 9, SQLi=2, XSS=): Last Matched Message: Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Last Matched Data: -auth-check,wp-a11y,wplink,jquery-"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7AJl-yzAAADu6eL8AAABL"]
2018:09:20-10:42:24 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Operator GE matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/modsecurity_crs_correlation.conf"] [line "37"] [id "981204"] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 9, SQLi=2, XSS=): Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7AJl-yzAAADu6eL8AAABL"]
2018:09:20-10:42:24 test-utm httpd: id="0299" srcip="-Source_IP-" localip="-Destination_IP-" size="41465" user="-" host="-Source_IP-" method="GET" statuscode="200" reason="-" extra="-" exceptions="-" time="42445" url="/wp-admin/load-scripts.php" server="-Destination_IP-" port="80" query="?c=1&load%5B%5D=hoverIntent,common,admin-bar,wp-ajax-response,jquery-color,wp-lists,quicktags,jquery-query,admin-comments,svg-painter,heartbeat,&load%5B%5D=wp-auth-check,wp-a11y,wplink,jquery-ui-core,jquery-ui-widget,jquery-ui-position,jquery-ui-menu,jquery-ui-autocomplete&ver=4.9.8" referer="http://-Destination_IP-/wp-admin/edit-comments.php" cookie="wordpress_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C6911a5e3e657015c25622aeb1ca4ddb1f5ab77ffc6edee88098e2c6cbce17b3c; wp-settings-time-1=1537269668; wordpress_test_cookie=WP+Cookie+check; wp-settings-1=hidetb%3D1%26post_dfw%3Doff%26editor%3Dhtml%26libraryContent%3Dbrowse; wordpress_logged_in_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct
2018:09:20-10:42:24 test-utm httpd: 5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C4e9f2092e9657611ff761890eef537ac490a7b4b924b016da91bc54ddd786ffb" set-cookie="-" uid="W6L7AJl-yzAAADu6eL8AAABL"
2018:09:20-10:42:26 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "^[\\\\d.:]+$" at REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_protocol_anomalies.conf"] [line "98"] [id "960017"] [rev "2"] [msg "Host header is a numeric IP address"] [data "-Destination_IP-"] [severity "WARNING"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "9"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [tag "http://technet.microsoft.com/en-us/magazine/2005.01.hackerbasher.aspx"] [hostname "-Destination_IP-"] [uri "/wp-admin/plugins.php"] [unique_id "W6L7Apl-yzAAADu6eMAAAABL"]
2018:09:20-10:42:26 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Rule 9d7d648 [id "981172"][file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"][line "157"] - Execution error - PCRE limits exceeded (-8): (null). [hostname "-Destination_IP-"] [uri "/wp-admin/plugins.php"] [unique_id "W6L7Apl-yzAAADu6eMAAAABL"]
2018:09:20-10:42:27 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Operator LT matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/modsecurity_crs_correlation.conf"] [line "33"] [id "981203"] [msg "Inbound Anomaly Score (Total Inbound Score: 3, SQLi=, XSS=): Host header is a numeric IP address"] [hostname "-Destination_IP-"] [uri "/wp-admin/plugins.php"] [unique_id "W6L7Apl-yzAAADu6eMAAAABL"]
2018:09:20-10:42:27 test-utm httpd: id="0299" srcip="-Source_IP-" localip="-Destination_IP-" size="13029" user="-" host="-Source_IP-" method="GET" statuscode="200" reason="-" extra="-" exceptions="-" time="1406183" url="/wp-admin/plugins.php" server="-Destination_IP-" port="80" query="" referer="http://-Destination_IP-/wp-admin/edit-comments.php" cookie="wordpress_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C6911a5e3e657015c25622aeb1ca4ddb1f5ab77ffc6edee88098e2c6cbce17b3c; wp-settings-time-1=1537269668; wordpress_test_cookie=WP+Cookie+check; wp-settings-1=hidetb%3D1%26post_dfw%3Doff%26editor%3Dhtml%26libraryContent%3Dbrowse; wordpress_logged_in_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C4e9f2092e9657611ff761890eef537ac490a7b4b924b016da91bc54ddd786ffb" set-cookie="-" uid="W6L7Apl-yzAAADu6eMAAAABL"
2018:09:20-10:42:27 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Warning. Pattern match "^[\\\\d.:]+$" at REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_protocol_anomalies.conf"] [line "98"] [id "960017"] [rev "2"] [msg "Host header is a numeric IP address"] [data "-Destination_IP-"] [severity "WARNING"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "9"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [tag "http://technet.microsoft.com/en-us/magazine/2005.01.hackerbasher.aspx"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7A5l-yzAAADu6eMEAAABa"]
2018:09:20-10:42:27 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Rule 9d7d648 [id "981172"][file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"][line "157"] - Execution error - PCRE limits exceeded (-8): (null). [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7A5l-yzAAADu6eMEAAABa"]
2018:09:20-10:42:27 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS:load[]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS:load[]: hoverIntent,common,admin-bar,underscore,wp-util,wp-a11y,updates,jquery-ui-core,thickbox,plugin-install,svg-painter,heartbeat,wp-"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7A5l-yzAAADu6eMEAAABa"]
2018:09:20-10:42:27 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Warning. Pattern match "(.*)" at TX:960017-OWASP_CRS/POLICY/IP_HOST-REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_inbound_blocking.conf"] [line "26"] [id "981176"] [msg "Inbound Anomaly Score Exceeded (Total Score: 6, SQLi=1, XSS=): Last Matched Message: Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Last Matched Data: -Destination_IP-"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7A5l-yzAAADu6eMEAAABa"]
2018:09:20-10:42:27 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Warning. Pattern match "(.*)" at TX:981173-OWASP_CRS/WEB_ATTACK/RESTRICTED_SQLI_CHARS-ARGS:load[]. [file "/usr/apache/conf/waf/modsecurity_crs_inbound_blocking.conf"] [line "26"] [id "981176"] [msg "Inbound Anomaly Score Exceeded (Total Score: 6, SQLi=1, XSS=): Last Matched Message: Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Last Matched Data: -bar,underscore,wp-util,wp-a11y,updates,jquery-"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7A5l-yzAAADu6eMEAAABa"]
2018:09:20-10:42:27 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Warning. Operator GE matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/modsecurity_crs_correlation.conf"] [line "37"] [id "981204"] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 6, SQLi=1, XSS=): Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [hostname "-Destination_IP-"] [uri "/wp-admin/load-scripts.php"] [unique_id "W6L7A5l-yzAAADu6eMEAAABa"]
2018:09:20-10:42:27 test-utm httpd: id="0299" srcip="-Source_IP-" localip="-Destination_IP-" size="30991" user="-" host="-Source_IP-" method="GET" statuscode="200" reason="-" extra="-" exceptions="-" time="32270" url="/wp-admin/load-scripts.php" server="-Destination_IP-" port="80" query="?c=1&load%5B%5D=hoverIntent,common,admin-bar,underscore,wp-util,wp-a11y,updates,jquery-ui-core,thickbox,plugin-install,svg-painter,heartbeat,wp-&load%5B%5D=auth-check&ver=4.9.8" referer="http://-Destination_IP-/wp-admin/plugins.php" cookie="wordpress_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C6911a5e3e657015c25622aeb1ca4ddb1f5ab77ffc6edee88098e2c6cbce17b3c; wp-settings-time-1=1537269668; wordpress_test_cookie=WP+Cookie+check; wp-settings-1=hidetb%3D1%26post_dfw%3Doff%26editor%3Dhtml%26libraryContent%3Dbrowse; wordpress_logged_in_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C4e9f2092e9657611ff761890eef537ac490a7b4b924b016da91bc54ddd786ffb" se
2018:09:20-10:42:27 test-utm httpd: t-cookie="-" uid="W6L7A5l-yzAAADu6eMEAAABa"
2018:09:20-10:42:29 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Warning. Pattern match "^[\\\\d.:]+$" at REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_protocol_anomalies.conf"] [line "98"] [id "960017"] [rev "2"] [msg "Host header is a numeric IP address"] [data "-Destination_IP-"] [severity "WARNING"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "9"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [tag "http://technet.microsoft.com/en-us/magazine/2005.01.hackerbasher.aspx"] [hostname "-Destination_IP-"] [uri "/wp-admin/users.php"] [unique_id "W6L7BZl-yzAAADu6eMIAAABa"]
2018:09:20-10:42:29 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Rule 9d7d648 [id "981172"][file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"][line "157"] - Execution error - PCRE limits exceeded (-8): (null). [hostname "-Destination_IP-"] [uri "/wp-admin/users.php"] [unique_id "W6L7BZl-yzAAADu6eMIAAABa"]
2018:09:20-10:42:29 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Warning. Operator LT matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/modsecurity_crs_correlation.conf"] [line "33"] [id "981203"] [msg "Inbound Anomaly Score (Total Inbound Score: 3, SQLi=, XSS=): Host header is a numeric IP address"] [hostname "-Destination_IP-"] [uri "/wp-admin/users.php"] [unique_id "W6L7BZl-yzAAADu6eMIAAABa"]
2018:09:20-10:42:29 test-utm httpd: id="0299" srcip="-Source_IP-" localip="-Destination_IP-" size="9369" user="-" host="-Source_IP-" method="GET" statuscode="200" reason="-" extra="-" exceptions="-" time="368091" url="/wp-admin/users.php" server="-Destination_IP-" port="80" query="" referer="http://-Destination_IP-/wp-admin/plugins.php" cookie="wp-settings-time-1=1537269668; wordpress_test_cookie=WP+Cookie+check; wp-settings-1=hidetb%3D1%26post_dfw%3Doff%26editor%3Dhtml%26libraryContent%3Dbrowse; wordpress_logged_in_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C4e9f2092e9657611ff761890eef537ac490a7b4b924b016da91bc54ddd786ffb; wordpress_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C6911a5e3e657015c25622aeb1ca4ddb1f5ab77ffc6edee88098e2c6cbce17b3c" set-cookie="-" uid="W6L7BZl-yzAAADu6eMIAAABa"
2018:09:20-10:42:30 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3810900848] [client -Source_IP-] ModSecurity: Warning. Pattern match "^[\\\\d.:]+$" at REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_protocol_anomalies.conf"] [line "98"] [id "960017"] [rev "2"] [msg "Host header is a numeric IP address"] [data "-Destination_IP-"] [severity "WARNING"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "9"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [tag "http://technet.microsoft.com/en-us/magazine/2005.01.hackerbasher.aspx"] [hostname "-Destination_IP-"] [uri "/wp-admin/options-general.php"] [unique_id "W6L7Bpl-yzAAADu6eMMAAABY"]
2018:09:20-10:42:30 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3810900848] [client -Source_IP-] ModSecurity: Rule 9d7d648 [id "981172"][file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"][line "157"] - Execution error - PCRE limits exceeded (-8): (null). [hostname "-Destination_IP-"] [uri "/wp-admin/options-general.php"] [unique_id "W6L7Bpl-yzAAADu6eMMAAABY"]
2018:09:20-10:42:31 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3810900848] [client -Source_IP-] ModSecurity: Warning. Operator LT matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/modsecurity_crs_correlation.conf"] [line "33"] [id "981203"] [msg "Inbound Anomaly Score (Total Inbound Score: 3, SQLi=, XSS=): Host header is a numeric IP address"] [hostname "-Destination_IP-"] [uri "/wp-admin/options-general.php"] [unique_id "W6L7Bpl-yzAAADu6eMMAAABY"]
2018:09:20-10:42:31 test-utm httpd: id="0299" srcip="-Source_IP-" localip="-Destination_IP-" size="18903" user="-" host="-Source_IP-" method="GET" statuscode="200" reason="-" extra="-" exceptions="-" time="1168412" url="/wp-admin/options-general.php" server="-Destination_IP-" port="80" query="" referer="http://-Destination_IP-/wp-admin/users.php" cookie="wp-settings-time-1=1537269668; wordpress_test_cookie=WP+Cookie+check; wp-settings-1=hidetb%3D1%26post_dfw%3Doff%26editor%3Dhtml%26libraryContent%3Dbrowse; wordpress_logged_in_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C4e9f2092e9657611ff761890eef537ac490a7b4b924b016da91bc54ddd786ffb; wordpress_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C6911a5e3e657015c25622aeb1ca4ddb1f5ab77ffc6edee88098e2c6cbce17b3c" set-cookie="-" uid="W6L7Bpl-yzAAADu6eMMAAABY"
2018:09:20-10:42:35 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Warning. Pattern match "^[\\\\d.:]+$" at REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_protocol_anomalies.conf"] [line "98"] [id "960017"] [rev "2"] [msg "Host header is a numeric IP address"] [data "-Destination_IP-"] [severity "WARNING"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "9"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [tag "http://technet.microsoft.com/en-us/magazine/2005.01.hackerbasher.aspx"] [hostname "-Destination_IP-"] [uri "/wp-admin/options-permalink.php"] [unique_id "W6L7C5l-yzAAADu6eMQAAABa"]
2018:09:20-10:42:35 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Rule 9d7d648 [id "981172"][file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"][line "157"] - Execution error - PCRE limits exceeded (-8): (null). [hostname "-Destination_IP-"] [uri "/wp-admin/options-permalink.php"] [unique_id "W6L7C5l-yzAAADu6eMQAAABa"]
2018:09:20-10:42:35 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3794115440] [client -Source_IP-] ModSecurity: Warning. Operator LT matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/modsecurity_crs_correlation.conf"] [line "33"] [id "981203"] [msg "Inbound Anomaly Score (Total Inbound Score: 3, SQLi=, XSS=): Host header is a numeric IP address"] [hostname "-Destination_IP-"] [uri "/wp-admin/options-permalink.php"] [unique_id "W6L7C5l-yzAAADu6eMQAAABa"]
2018:09:20-10:42:35 test-utm httpd: id="0299" srcip="-Source_IP-" localip="-Destination_IP-" size="8774" user="-" host="-Source_IP-" method="GET" statuscode="200" reason="-" extra="-" exceptions="-" time="379844" url="/wp-admin/options-permalink.php" server="-Destination_IP-" port="80" query="" referer="http://-Destination_IP-/wp-admin/options-general.php" cookie="wordpress_test_cookie=WP+Cookie+check; wp-settings-1=hidetb%3D1%26post_dfw%3Doff%26editor%3Dhtml%26libraryContent%3Dbrowse; wordpress_logged_in_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C4e9f2092e9657611ff761890eef537ac490a7b4b924b016da91bc54ddd786ffb; wordpress_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C6911a5e3e657015c25622aeb1ca4ddb1f5ab77ffc6edee88098e2c6cbce17b3c; wp-settings-time-1=1537269668" set-cookie="-" uid="W6L7C5l-yzAAADu6eMQAAABa"
2018:09:20-10:42:39 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3810900848] [client -Source_IP-] ModSecurity: Warning. Pattern match "^[\\\\d.:]+$" at REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_protocol_anomalies.conf"] [line "98"] [id "960017"] [rev "2"] [msg "Host header is a numeric IP address"] [data "-Destination_IP-"] [severity "WARNING"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "9"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [tag "http://technet.microsoft.com/en-us/magazine/2005.01.hackerbasher.aspx"] [hostname "-Destination_IP-"] [uri "/wp-admin/edit.php"] [unique_id "W6L7D5l-yzAAADu6eMUAAABY"]
2018:09:20-10:42:39 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3810900848] [client -Source_IP-] ModSecurity: Rule 9d7d648 [id "981172"][file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"][line "157"] - Execution error - PCRE limits exceeded (-8): (null). [hostname "-Destination_IP-"] [uri "/wp-admin/edit.php"] [unique_id "W6L7D5l-yzAAADu6eMUAAABY"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3810900848] [client -Source_IP-] ModSecurity: Warning. Operator LT matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/modsecurity_crs_correlation.conf"] [line "33"] [id "981203"] [msg "Inbound Anomaly Score (Total Inbound Score: 3, SQLi=, XSS=): Host header is a numeric IP address"] [hostname "-Destination_IP-"] [uri "/wp-admin/edit.php"] [unique_id "W6L7D5l-yzAAADu6eMUAAABY"]
2018:09:20-10:42:40 test-utm httpd: id="0299" srcip="-Source_IP-" localip="-Destination_IP-" size="12372" user="-" host="-Source_IP-" method="GET" statuscode="200" reason="-" extra="-" exceptions="-" time="505373" url="/wp-admin/edit.php" server="-Destination_IP-" port="80" query="?post_type=page" referer="http://-Destination_IP-/wp-admin/options-permalink.php" cookie="wordpress_test_cookie=WP+Cookie+check; wp-settings-1=hidetb%3D1%26post_dfw%3Doff%26editor%3Dhtml%26libraryContent%3Dbrowse; wordpress_logged_in_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C4e9f2092e9657611ff761890eef537ac490a7b4b924b016da91bc54ddd786ffb; wordpress_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C6911a5e3e657015c25622aeb1ca4ddb1f5ab77ffc6edee88098e2c6cbce17b3c; wp-settings-time-1=1537269668" set-cookie="-" uid="W6L7D5l-yzAAADu6eMUAAABY"
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "^[\\\\d.:]+$" at REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_protocol_anomalies.conf"] [line "98"] [id "960017"] [rev "2"] [msg "Host header is a numeric IP address"] [data "-Destination_IP-"] [severity "WARNING"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "9"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [tag "http://technet.microsoft.com/en-us/magazine/2005.01.hackerbasher.aspx"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Rule 9d7d648 [id "981172"][file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"][line "157"] - Execution error - PCRE limits exceeded (-8): (null). [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS_NAMES:data[wp-check-locked-posts][]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS_NAMES:data[wp-check-locked-posts][]: data[wp-check-locked-posts][]"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS_NAMES:data[wp-check-locked-posts][]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS_NAMES:data[wp-check-locked-posts][]: data[wp-check-locked-posts][]"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS_NAMES:data[wp-check-locked-posts][]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS_NAMES:data[wp-check-locked-posts][]: data[wp-check-locked-posts][]"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS_NAMES:data[wp-check-locked-posts][]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS_NAMES:data[wp-check-locked-posts][]: data[wp-check-locked-posts][]"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS_NAMES:data[wp-check-locked-posts][]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS_NAMES:data[wp-check-locked-posts][]: data[wp-check-locked-posts][]"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS_NAMES:data[wp-check-locked-posts][]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS_NAMES:data[wp-check-locked-posts][]: data[wp-check-locked-posts][]"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "([\\\\~\\\\!\\\\@\\\\#\\\\$\\\\%\\\\^\\\\&\\\\*\\\\(\\\\)\\\\-\\\\+\\\\=\\\\{\\\\}\\\\[\\\\]\\\\|\\\\:\\\\;\\"\\\\'\\\\\\xc2\\xb4\\\\\\xe2\\x80\\x99\\\\\\xe2\\x80\\x98\\\\`\\\\<\\\\>].*?){4,}" at ARGS_NAMES:data[wp-check-locked-posts][]. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "159"] [id "981173"] [rev "2"] [msg "Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Matched Data: - found within ARGS_NAMES:data[wp-check-locked-posts][]: data[wp-check-locked-posts][]"] [ver "OWASP_CRS/2.2.7"] [maturity "9"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "(.*)" at TX:960017-OWASP_CRS/POLICY/IP_HOST-REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_inbound_blocking.conf"] [line "26"] [id "981176"] [msg "Inbound Anomaly Score Exceeded (Total Score: 24, SQLi=7, XSS=): Last Matched Message: Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Last Matched Data: -Destination_IP-"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Pattern match "(.*)" at TX:981173-OWASP_CRS/WEB_ATTACK/RESTRICTED_SQLI_CHARS-ARGS_NAMES:data[wp-check-locked-posts][]. [file "/usr/apache/conf/waf/modsecurity_crs_inbound_blocking.conf"] [line "26"] [id "981176"] [msg "Inbound Anomaly Score Exceeded (Total Score: 24, SQLi=7, XSS=): Last Matched Message: Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [data "Last Matched Data: [wp-check-locked-"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd[15290]: [security2:error] [pid 15290:tid 3920006000] [client -Source_IP-] ModSecurity: Warning. Operator GE matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/modsecurity_crs_correlation.conf"] [line "37"] [id "981204"] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 24, SQLi=7, XSS=): Restricted SQL Character Anomaly Detection Alert - Total # of special characters exceeded"] [hostname "-Destination_IP-"] [uri "/wp-admin/admin-ajax.php"] [unique_id "W6L7EJl-yzAAADu6eMYAAABL"]
2018:09:20-10:42:40 test-utm httpd: id="0299" srcip="-Source_IP-" localip="-Destination_IP-" size="47" user="-" host="-Source_IP-" method="POST" statuscode="200" reason="-" extra="-" exceptions="-" time="380459" url="/wp-admin/admin-ajax.php" server="-Destination_IP-" port="80" query="" referer="http://-Destination_IP-/wp-admin/edit.php?post_type=page" cookie="wordpress_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C6911a5e3e657015c25622aeb1ca4ddb1f5ab77ffc6edee88098e2c6cbce17b3c; wp-settings-time-1=1537269668; wordpress_test_cookie=WP+Cookie+check; wp-settings-1=hidetb%3D1%26post_dfw%3Doff%26editor%3Dhtml%26libraryContent%3Dbrowse; wordpress_logged_in_1e63e35c63580160e360c0bc47a51f92=hyper-wdprs%7C1537580508%7Ct5i4qj8wvqfW9gjr2ujcwyZTtKwldu1P1lpDLSLI38o%7C4e9f2092e9657611ff761890eef537ac490a7b4b924b016da91bc54ddd786ffb" set-cookie="-" uid="W6L7EJl-yzAAADu6eMYAAABL"
ライブログに出力されたルールIDを確認
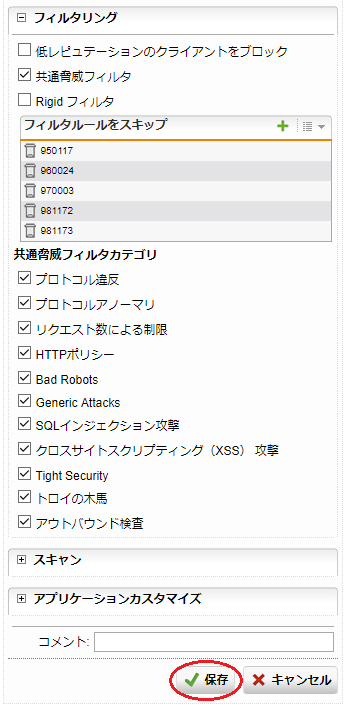
- ライブログに出力されたルールIDは、下記の8つで、そのうち3つのルールIDはインフラストラクチャルールになります。
※インフラストラクチャルールにつきましては後ほど説明します。
[id "950117"] [id "960024"] [id "970003"] [id "981172"] [id "981173"] [id "981176"] ←インフラストラクチャルール [id "981203"] ←インフラストラクチャルール [id "981204"] ←インフラストラクチャルール
- 検出されたルールIDのうち下記の5つを「フィルタルールのスキップ」リストに追加します。
[id "950117"] [id "960024"] [id "970003"] [id "981172"] [id "981173"]
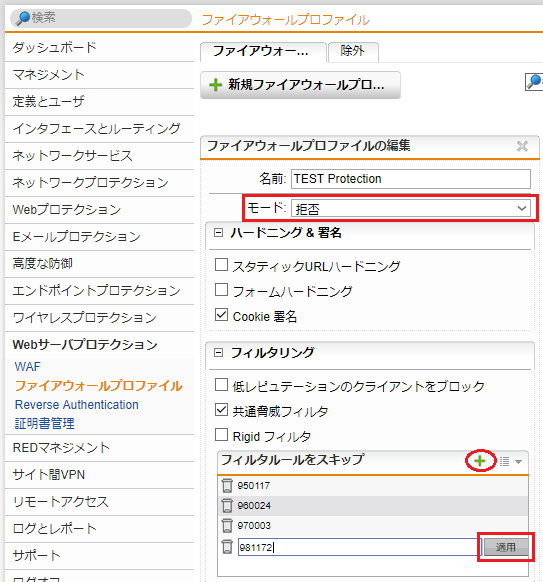
「フィルタルールのスキップ」へ、誤検出のルールIDを追加
- Webサーバプロテクション > ファイアウォールプロファイル > ファイアウォールプロファイル タブをクリックし、先ほど作成した「TEST Protection」の「編集」ボタンをクリックします。

- 「モード」を拒否に変更、「フィルタルールのスキップ」の「 + 」をクリックし、スキップするルールIDを入力して「適用」ボタンをクリックします。

- 5つのルールIDを入力後に「保存」ボタンをクリックします。

インフラストラクチャルールについて
入力するルールIDによって、警告メッセージが表示される場合があります。例として、[id "981176"] を追加した状態を紹介します。
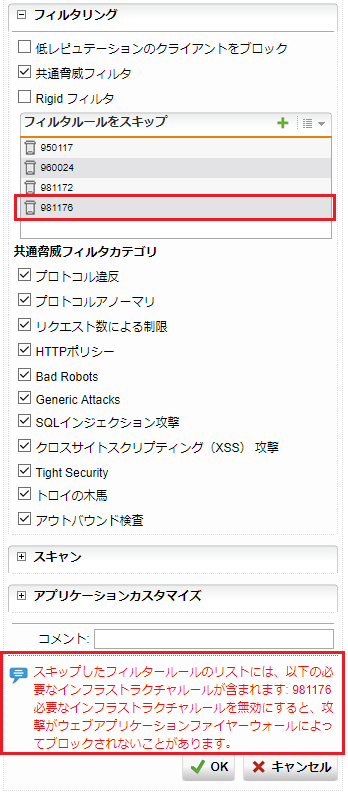
「保存」ボタンをクリックすると、赤い文字で下記のように警告されます。
---------------------------------------------------------------------------------------------------------------------------------
スキップしたフィルタールールのリストには、
以下の必要なインフラストラクチャルールが含まれます: 981176
必要なインフラストラクチャルールを無効にすると、
攻撃がウェブアプリケーションファイヤーウォールによってブロックされないことがあります。
---------------------------------------------------------------------------------------------------------------------------------
WAFのルールは攻撃のカテゴリごとに依存関係を持っており、インフラストラクチャルールとは「その中でも根幹となる重要なルール」です。「フィルタルールのスキップ」には、非インフラストラクチャルールのみ入力されることをお勧めします。
以下にインフラストラクチャルールのルールIDを示します。
981020 981021 981022 981175 981176 981200 981201 981202 981203 981204 981205
WAFの動作確認
ひととおりWAFの設定が完了しましたので、攻撃を実行して反応を確認したいと思います。
「wp-login.php」に、クロスサイトスクリプティング攻撃を行います。具体的な攻撃方法の解説は省略します。
http://Sophos UTM に付与されたグローバルIPアドレス/wp-login.php
攻撃後のWAFのライブログを見てみましょう。
※送信元のIPを「-Source_IP-」、Sophos UTM のグローバルIPを「-Destination_IP-」に変更してあります。
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Warning. Pattern match "(?i)(]*>[\\\\s\\\\S]*?<\\\\/script[^>]*>|<script[^>]*>[\\\\s\\\\S]*?<\\\\/script[[\\\\s\\\\S]]*[\\\\s\\\\S]|<script[^>]*>[\\\\s\\\\S]*?<\\\\/script[\\\\s]*[\\\\s]|<script[^>]*>[\\\\s\\\\S]*?<\\\\/script|<script[^>]*>[\\\\s\\\\S]*?)" at ARGS:log. [file "/usr/apache/conf/waf/modsecurity_crs_xss_attacks.conf"] [line "14"] [id "973336"] [rev "1"] [msg "XSS Filter - Category 1: Script Tag Vector"] [data "Matched Data: <script><alert('XSS');> found within ARGS:log: <alert('XSS');>"] [severity "CRITICAL"] [ver "OWASP_CRS/2.2.7"] [maturity "1"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/XSS"] [tag "WASCTC/WASC-8"] [tag "WASCTC/WASC-22"] [tag "OWASP_TOP_10/A2"] [tag "OWASP_AppSensor/IE1"] [tag "PCI/6.5.1"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Warning. Pattern match "\\\\balert\\\\b\\\\W*?\\\\(" at ARGS:log. [file "/usr/apache/conf/waf/modsecurity_crs_xss_attacks.conf"] [line "163"] [id "958052"] [rev "2"] [msg "Cross-site Scripting (XSS) Attack"] [data "Matched Data: alert( found within ARGS:log: <alert('xss');>"] [severity "CRITICAL"] [ver "OWASP_CRS/2.2.7"] [maturity "8"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/XSS"] [tag "WASCTC/WASC-8"] [tag "WASCTC/WASC-22"] [tag "OWASP_TOP_10/A2"] [tag "OWASP_AppSensor/IE1"] [tag "PCI/6.5.1"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Warning. Pattern match "\\\\< ?script\\\\b" at ARGS:log. [file "/usr/apache/conf/waf/modsecurity_crs_xss_attacks.conf"] [line "211"] [id "958051"] [rev "2"] [msg "Cross-site Scripting (XSS) Attack"] [data "Matched Data: <alert('xss');>"] [severity "CRITICAL"] [ver "OWASP_CRS/2.2.7"] [maturity "8"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/XSS"] [tag "WASCTC/WASC-8"] [tag "WASCTC/WASC-22"] [tag "OWASP_TOP_10/A2"] [tag "OWASP_AppSensor/IE1"] [tag "PCI/6.5.1"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Warning. Pattern match "<(a|abbr|acronym|address|applet|area|audioscope|b|base|basefront|bdo|bgsound|big|blackface|blink|blockquote|body|bq|br|button|caption|center|cite|code|col|colgroup|comment|dd|del|dfn|dir|div|dl|dt|em|embed|fieldset|fn|font|form|frame|frameset|h1|head|h ..." at ARGS:log. [file "/usr/apache/conf/waf/modsecurity_crs_xss_attacks.conf"] [line "301"] [id "973300"] [rev "2"] [msg "Possible XSS Attack Detected - HTML Tag Handler"] [data "Matched Data: found within ARGS:log: <script><alert('xss');>"] [ver "OWASP_CRS/2.2.7"] [maturity "8"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/XSS"] [tag "WASCTC/WASC-8"] [tag "WASCTC/WASC-22"] [tag "OWASP_TOP_10/A2"] [tag "OWASP_AppSensor/IE1"] [tag "PCI/6.5.1"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Warning. Pattern match "(fromcharcode|alert|eval)\\\\s*\\\\(" at ARGS:log. [file "/usr/apache/conf/waf/modsecurity_crs_xss_attacks.conf"] [line "391"] [id "973307"] [rev "2"] [msg "XSS Attack Detected"] [data "Matched Data: alert( found within ARGS:log: <alert('xss');>"] [ver "OWASP_CRS/2.2.7"] [maturity "8"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/XSS"] [tag "WASCTC/WASC-8"] [tag "WASCTC/WASC-22"] [tag "OWASP_TOP_10/A2"] [tag "OWASP_AppSensor/IE1"] [tag "PCI/6.5.1"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Warning. Pattern match "[/'\\"<]xss[/'\\">]" at ARGS:log. [file "/usr/apache/conf/waf/modsecurity_crs_xss_attacks.conf"] [line "432"] [id "973310"] [rev "2"] [msg "XSS Attack Detected"] [data "Matched Data: 'xss' found within ARGS:log: <alert('xss');>"] [ver "OWASP_CRS/2.2.7"] [maturity "8"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/XSS"] [tag "WASCTC/WASC-8"] [tag "WASCTC/WASC-22"] [tag "OWASP_TOP_10/A2"] [tag "OWASP_AppSensor/IE1"] [tag "PCI/6.5.1"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Warning. Pattern match "(?i:)" at ARGS:log. [file "/usr/apache/conf/waf/modsecurity_crs_xss_attacks.conf"] [line "472"] [id "973331"] [rev "2"] [msg "IE XSS Filters - Attack Detected."] [data "Matched Data: <script> found within ARGS:log: <script><alert('XSS');>"] [ver "OWASP_CRS/2.2.7"] [maturity "8"] [accuracy "8"] [tag "OWASP_CRS/WEB_ATTACK/XSS"] [tag "WASCTC/WASC-8"] [tag "WASCTC/WASC-22"] [tag "OWASP_TOP_10/A2"] [tag "OWASP_AppSensor/IE1"] [tag "PCI/6.5.1"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Warning. Pattern match "(?i:(?:[\\"'`\\xc2\\xb4\\xe2\\x80\\x99\\xe2\\x80\\x98]\\\\s*?\\\\*.+(?:x?or|div|like|between|and|id)\\\\W*?[\\"'`\\xc2\\xb4\\xe2\\x80\\x99\\xe2\\x80\\x98]\\\\d)|(?:\\\\^[\\"'`\\xc2\\xb4\\xe2\\x80\\x99\\xe2\\x80\\x98])|(?:^[\\\\w\\\\s\\"'`\\xc2\\xb4\\xe2\\x80\\x99\\xe2\\x80\\x98-]+(?<=and\\\\s)(?<=or|xor ..." at ARGS:log. [file "/usr/apache/conf/waf/modsecurity_crs_sql_injection_attacks.conf"] [line "245"] [id "981243"] [msg "Detects classic SQL injection probings 2/2"] [data "Matched Data: <alert('X found within ARGS:log: <alert('XSS');>"] [severity "CRITICAL"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Access denied with code 403 (phase 2). Pattern match "(.*)" at TX:960017-OWASP_CRS/POLICY/IP_HOST-REQUEST_HEADERS:Host. [file "/usr/apache/conf/waf/modsecurity_crs_inbound_blocking.conf"] [line "26"] [id "981176"] [msg "Inbound Anomaly Score Exceeded (Total Score: 43, SQLi=1, XSS=35): Last Matched Message: 981243-Detects classic SQL injection probings 2/2"] [data "Last Matched Data: -Destination_IP-"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd[13299]: [security2:error] [pid 13299:tid 3836078960] [client -Source_IP-] ModSecurity: Warning. Operator GE matched 5 at TX:inbound_anomaly_score. [file "/usr/apache/conf/waf/modsecurity_crs_correlation.conf"] [line "37"] [id "981204"] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 43, SQLi=1, XSS=35): 981243-Detects classic SQL injection probings 2/2"] [hostname "-Destination_IP-"] [uri "/wp-login.php"] [unique_id "W6MP2Jl-yzAAADPzHDgAAABV"]
2018:09:20-12:11:20 test-utm httpd: id="0299" srcip="-Source_IP-" localip="-Destination_IP-" size="221" user="-" host="-Source_IP-" method="POST" statuscode="403" reason="waf" extra="Inbound Anomaly Score Exceeded (Total Score: 43, SQLi=1, XSS=35): Last Matched Message: 981243-Detects classic SQL injection probings 2/2" exceptions="-" time="9692" url="/wp-login.php" server="-Destination_IP-" port="80" query="" referer="http://-Destination_IP-/wp-login.php" cookie="wordpress_test_cookie=WP+Cookie+check; HASH_wordpress_test_cookie=6933FB821B7169B5EFF1C73B7F136AC56CA5303C" set-cookie="-" uid="W6MP2Jl-yzAAADPzHDgAAABV"
「XSS Attack Detected」とクロスサイトスクリプティング攻撃が検出され、「Access denied with code 403」で、アクセスを拒否して ステータスコード403 を返したことが出力されています。
ブラウザの表示は下記になります。
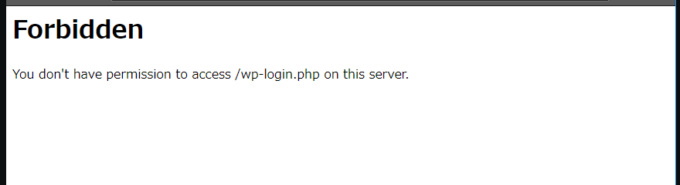
バックエンドに設置した「wordpress-server」が Sophos UTM の WAF機能により、攻撃から保護されていることを確認できました。
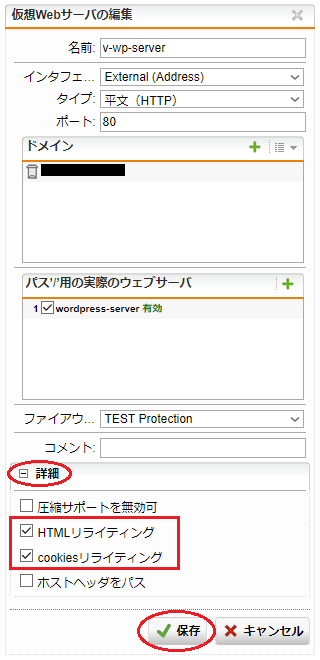
仮想Webサーバの設定についての補足
仮想Webサーバは、指定したバックエンドWebサーバのリバースプロキシとして動作します。この仕様により、サイトの作りによっては表示遅延や、表示崩れ等が発生する場合があります。
WAF使用の際、サイトの表示に問題が生じた場合は、該当する仮想Webサーバを編集します。「詳細」をクリックし、「HTMLリライティング」と「cookiesリライティング」にチェックを入れ、「保存」ボタンをクリックした後、再びサイトの表示を試してみてください。
今回はここまで
今回のWAF設定は情報量が多くなり、複雑な印象をもった方もいると思いますが、段階を踏んで下記の5段階の工程を行えば、設定は難しくありません。
- ファイアウォールプロファイルの作成
- バックエンドWebサーバの作成
- 仮想Webサーバの作成
- 正常系アクセスのテスト、WAFのライブログを確認
- 「フィルタルールのスキップ」リストへ、誤検出のルールIDの追加
次回は、Webサーバプロテクション WAF設定の続きで、バックエンドWebサーバのロードバランスについて紹介させて頂く予定です。